A user with IP address 37.115.188.126 has been locked out from the signing in or using the password recovery form for the following reason: Exceeded the maximum number of login failures which is: 20. The last username they tried to sign in with was: ‘admin’
User IP: 37.115.188.126
User hostname: 37-115-188-126-broadband.kyivstar.net
(That’s right! ‘admin’ isn’t a valid username on this blog and it shouldn’t be on yours, either! Here’s how to change your ‘admin’ username as well as usernames to avoid when configuring WordPress.)
I looked for a variety of ways to block this, and ultimately decided to do it based on IP address. Through a little research I found that Kyivstar has 14 different IPv4 origin ranges, so they all needed to be blocked individually. Fortunately, this is possible through the WordFence Plugin.
If you’re not using WordFence, go install it right now. They have a free version that offers a ton of functionality but upgrading to the pro version is certainly worthwhile in my opinion.
Blocking IP Address Ranges in WordFence
Blocking IP address ranges in WordFence is easy. Simply go to WordFence >> Advanced Blocking and there is an input for the IP address range. You’ll need to enter all 14 of the following ranges individually. I named them all “Kyivstar Block X of Y” but you can give them whatever name you want.
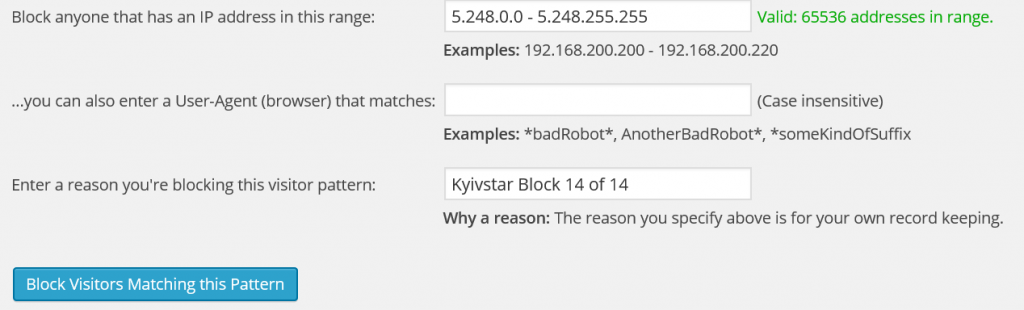
The 14 IP address ranges that you need to block are:
- 5.248.0.0 – 5.248.255.255
- 37.115.0.0 – 37.115.255.255
- 37.229.0.0 – 37.229.255.255
- 46.118.0.0 – 46.119.255.255
- 46.185.0.0 – 46.185.127.255
- 46.211.0.0 – 46.211.255.255
- 81.23.16.0 – 81.23.31.255
- 94.153.0.0 – 94.153.255.255
- 134.249.0.0 – 134.249.255.255
- 109.162.0.0 – 109.162.127.255
- 176.8.0.0 – 176.8.255.255
- 178.137.0.0 – 178.137.255.255
- 188.163.64.0 – 188.163.127.255
- 193.41.60.0 – 193.41.63.255
Warning: This will block 709,632 IP addresses! That’s a ton of addresses, but in this case it was worth it because we have no legitimate traffic originating from these IPs. The focus of the particular series of blogs that I’m securing is for a particular demographic of people who are largely based in the United States, so blocking traffic from the Ukraine isn’t a huge concern. We figure that odds of a blog reader being on vacation in the Ukraine and happening to use Kyivstar for internet AND getting angry because they can’t access the blog is low.
There are always tradeoffs, and this was an acceptable one for us.
It certainly would have been easier to block on hostname, but there are two problems with this:
- WordFence doesn’t have this capability
- It would require a reverse DNS lookup on each IP address which would be a huge load on the server which would negatively impact page load times which could hurt SEO ranking.
It’s my guess that WordFence doesn’t have hostname blocking for this very reason, but that’s speculation on my part.
Recap
This is a pretty simple way to block traffic from a broadband connection that dynamically assigns IP addresses to its customers. The same approach could be used to block any ISP, but be extra careful to make sure you’re not blocking legitimate traffic to your blog.





16 Comments
We had the same thing along with them using email harvesters to get at some of our users. Gotta like creating a good honey pot to catch them.
Thank you for this! I started getting these attacks on Wednesday and it was driving me crazy. IPs all blocked now.
Hi,
I still have attack of lvv.broadband.kyivstar.net… With 178-137-95-227… I had have 4 attack for this afternoon and this evening… I have change Login and Password and… I had Wordfence… Luckily
Blocking 178.137.0.0 – 178.137.255.255 should knock out that IP address from being able to access your site. Just make sure you do the other 13 as well!
Thank you! These guys have been soaking up my writing time for a while now.
Cheers for this post, hopefully it will prevent the numerous attempts to hack my wordpress blog that have been occurring over the past few months, just need to stop all the Chinese hackers now 🙁
Are all of the attempts coming from the same ISP in China? If so, you can use the same approach to block that entire ISP.
Belated response, yes quite a lot of them were and I’ve blocked most of the ranges now 🙂
Thank you Dave. Just what I needed today – and our attacks just began in the last day or so. Wordfence rocks – but I’d never used the ip range advanced blocking method before. Thanks again and have a wonderful 2015!!
Dave,
Thank you so much for the info and IP address range. Much appreciated.
I just use ip2locate and block the whole country period china too
Much appreciated!
Thanks, Dave! I had just been manually blocking them on an individual IP basis each time Wordfence alerted me of a login attempt. This method of limiting entire blocks of IP addresses works much better. Thanks for the putting it together.
Thank you i have locked that range of IP addresses from accessing my forum.
Thanks dave for the awsome limit, was facing attacks from past week and it was difficult blocking individual ip’s. Using aws, so blocked them using NACL
Glad it helped!